tia® Content Server (classic)
- Getting started (CS)
- Installation & Updating (CS)
- Configuration (CS)
- SAP-Customizing & ArchiveLink Security (CS)
- Logging (CS)
- Troubleshooting (CS)
- Changelog (CS)
- Version History & End-of-Life Dates (CS)
tia® Content Server (referred to as tia® CS) is a Java® developed software-application for the archiving and display of documents and data using the standard protocols SAP ArchiveLink® und SAP ILM. tia® CS is operated and managed as a servlet within a web server runtime environment. Documents and data are quickly and easily stored on any file system or common storage system (incl. NetApp®, EMC® Centera or iCAS® by iTernity) using the help through tia® CS. The use of a database can be eliminated due to the intelligent way tia® CS handles the storage of data. For the system requirements please see: Prerequisites for tia® and kgs Software Components In order to use tia® CS please follow the guide for requesting licences: KGS Software licensingIntroduction
System Requirements
General information
Licensing
Our product is delivered as a Web Archive Container (WAR file). This container can be directly installed (deployed). The deployment is dependent on the used web server. In order to install tia® Content Server on an Apache Tomcat web server please follow this guide: Installation Example: Apache Tomcat In order to update the bundles on top of which Content Server has been built please follow this guide: Updating tia® server solutionsInstallation & Updating Content Server
Example installation using Apache Tomcat
Generic update guide
Configuration
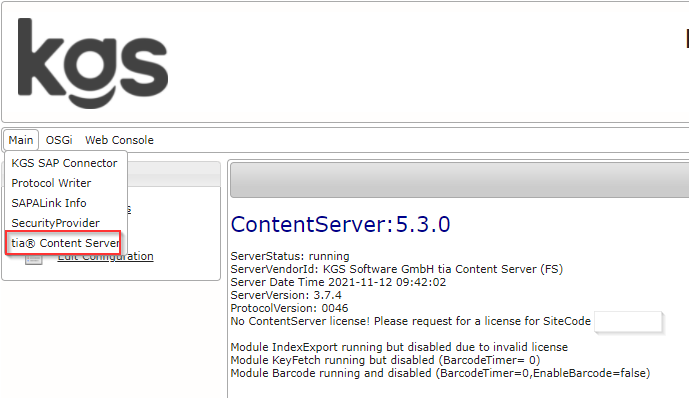
Please refer to this article, for an instruction to access the WebGUI: Using the KGS Application Framework Web Console (WebGUI) The kgs Application Framework Web Console provides configuration of basic settings, including working directory, debug level, and so on. The KGS Viewer Bundle configuration can be accessed from the menu Main → tia® Content Server. Now click on Edit Configuration under Administration. Save the configuration changes with . Edit Configuration (Main → tia® Content Server, Edit Configuration) For general information about the .cfg file handling please refer to this article: KGS application configuration files (.cfg) The revelant .cfg files for the ContentServer are inside the contentserver subfolder. Main configuration The file ContentServer.cfg contains the parameters for the main configuration. Repository configuration Files like CS-Repositories.example.cfg contain the Repository specific configuration. (Here for the Repository "example") To create a Repository .cfg file either use the Add Repository button or use the file CS-Repositories.example.cfg from the conf examples folder inside your product download.Configuration variants
Configuration via WebUI
Configuration using configuration files (.cfg)
Configuration options in the web userinterface
Within the License-tab you may enter license keys provided by KGS. The following license keys are possible at the moment. License Key String KGS license key. Necessary for running the KGS CS. IndexLicenseKey String Optional license key for the activation of the SAP IndexExport function. ILMLicenseKey String Optional license key for the activation of the SAP ILM function. Within the Barcode-tab you enable or disable the barcode SAP ArchiveLink functionality. Enable Barcode Checkbox Activation of the SAP ArchiveLink barcode function. Inactive Depending on your scenario and needs you may define in the Protocol-tab the following options which allow you to log certain ArchiveLink commands, that have been processed by ContentServer4Storage. Enable Protcol Checkbox Enable logging using the KGS ProtocolWriter. Inactive Enable Component Info Checkbox Enable logging of Component Info request. Inactive Protocol Alias String Alias of the KGS CS instance in the KGS ProtocolWriter. serverInfo Checkbox Enable logging of serverInfo requests. Inactive info Checkbox Enable logging info requests. Inactive get Checkbox Enable logging of get requests. Inactive create Checkbox Enable logging of create requests. Inactive docGet Checkbox Enable logging of docGet requests. Inactive mCreate Checkbox Enable logging of mCreate requests. Inactive append Checkbox Enable logging of append requests. Inactive delete Checkbox Enable logging of delete requests. Inactive lock Checkbox Enable logging of lock requests. Inactive update Checkbox Enable logging of update requests. Inactive putCert Checkbox Enable logging of putCert requests. Inactive search Checkbox Enable logging of search requests. Inactive adminContrep Checkbox Enable logging of adminContrep requests. Inactive attrSearch Checkbox Enable logging of attrSearch requests. Inactive Within the Common-tab you may define parameters that are directly related to ContentServer4Storage like debug levels or the working directory. The following parameters are currently supported. Config File String File name of the KGS CS configuration file. Only used for legacy parameters. Contentserver-conf.txt Config Directory String Directory of the previously specified configuration file. <servlet_home>\conf\contentserver Working Directory String Work directory for temporary data files. <servlet_home>\work\contentserver Debug Int Log Level 0: Logging disabled 1: Only errors 2: Errors and warnings 3: Errors, warnings and info 4: All, including debug 4 Max Process Count Int Number of maximum permitted object instances. Used for connections to the DMS via LinkOpen events. 0: No limitation 0 Disable Delete Commands Checkbox Delete requests will not be processed/rejected by the KGS CS. Inactive Force Component Return Checkbox When this parameter is activated, a component will always be delivered when processing a GET-request that does not specify a component ID, even if there is no data or data1 component to the document. The to be delivered components are determined by an exclusion procedure. The following components will not be delivered: Inactive Backend Read Timeout (s) Int Timeout in seconds until a read access to the DMS is terminated (thread interrupt). ( See DMSPool and parallelism in connection with SAPALink) 0 Backend Write Timeout (s) Int Timeout in seconds until a write access to the DMS is terminated (thread interrupt). (See DMSPool and parallelism in connection with SAPALink) 0 SAPMimeExtentionLookup Checkbox When activated, the MimeType and the document type are determined and saved in SAP according to the customizing of document types (transaction 0AD2, table TOADD). Inactive Min Process Count Int Number of lowest permitted object instances. A value greater then 0 will prevent the close of the last connection to the DMS. 0: no limitation 0 Support MTA Documents Checkbox When activated, MTA documents are supported. (Special handling for DocIDs with a "MTA" in it) Inactive In the Security-tab you may change settings related to the security configuration of ContentServer4Storage. The following parameters are supported. Default Security Int Default setting for Content-Repositories. 0: Security inactive 1: Security active & certificates are automatically activated after a putCert-Request. 2: Security active & certificates aren't automatically activated after a putCert-Request. The certificate must be activated with the CSAdmin in the transaction OAC0. This parameter can be defined Content-Repository specific. Initial Certificate Store Password String Initial KeyStore password. Should not be changed after deployment. SecurityChangeOnCommand CSV list of ArchiveLink requests (non-case sensitive), e.g. create, delete, update, etc. When a request that is maintained in this list arrives, the value set in the Secutity parameter is inverted to process this request. Example 1: Security=2 → the SecKey procedure is acive. SecurityChangeOnCommand=get,delete,info The incoming GET request is processed WITHOUT checking the SecKeys incl. Expiration. Example 2: Security=0 → the SecKey procedure is not active. SecurityChangeOnCommand=get,delete,info The incoming GET request is processed WITH examination of the SecKeys incl. Expiration. This parameter can be defined Content-Repository specific. Allowed Clients Only the clients specified here (IPs or hostnames) may write to the archive (create, update etc.). If no client is specified, all clients may write. The parameter is to be created as a CSV list. If a client is not listed, they receive the RC 401 → unauthorized. Allowed seperators for multiple IP-Addresses are ; (semikolon) or , (comma). The last IP segment can be used a wildcard. For example; ContentServer.AllowedClients=sapadm,192.168.1.2,192.168.2.* This parameter can be defined Content-Repository specific. Allowed CSAdmin Clients Only the IP addresses or hostnames specified here (SAP server) are authorized to use the CSAdmin function in SAP. Requests from other IPs or hosts receive the RC 401 → unauthorized. This parameter is to be created as a CSV list. The last IP segment can be used a wildcard. For example; ContentServer.AllowedCSAdmin=sapadm,192.168.1.2,192.168.2.* This parameter can be defined Content-Repository specific. Only the IP addresses or hostnames are allowed to use the X-Forward-For Header. It can be a comma separated list. Wildcards are allowed. For example: 192.168.1.2, 192.168.2.* Is no ReverseProxy in use, this Setting should be set to "None" Otherwise another Client can pretend to be a valid Host (for example with an IP-Address of the SAP System in the X-Forward-For Header). Only trusted Servers (Like ReverseProxies etc.) should be allowed to use the Header. Default: * - Every client is allowed to use the X-Forward-For Header. Default Document Protection String Default value for the DocProtection variable, if it does not exist in the http request. Usually this is part of the SAP http request. r: read u: update c: create d: delete Keystore Path String Path to the used KeyStore. Leave empty for default. The RFC tab contains the required parameters for the SAP-RFC communication (using the Barcode and IndexExport functions). The connection parameters can also be defined Content Repository specific. RFC connection Dropdown Select the RFC connection configured in the KGS SAP Connector For older versions You may set parameters in the Components-tab that define, how ContentServer4Storage handles components. Sign and Verify Content Checkbox Creates a hash value and signs this with a timestamp. When the data is called, the hash value is verified against the signature. This parameter can be defined Content-Repository specific. Inactive Hidden Components (info,docGet) String The components defined here are not returned when calling the info and docGet commands. SecurityProvider Dropdown list Currently only timestamp signatures with certificate are available. This parameter can be defined Content-Repository specific. TrustedTimestamp with Certificate Compression Mime Types String CSV list of MimeTypes that should be compressed. If this parameter is not defined, the compression will be applied to all MimeTypes (=*). For example; CompressMimeType=application/pdf,image/tiff Apart from MimeTypes, document types can also be defined, if the SAPMimeExtentionLookup parameter was configured. The MimeType for the document category is then determined by RFC using the SAP table TOADD. This parameter can be defined Content-Repository specific. Compression Size (Mb) Double Defines that components equal or greater than the value specified here (in MB) should be compressed. This function is only supported if the DMS supports the “DMS_COMP_PROPERTY_COMPRESSI ONSTRING” property. For example: 1 → 1 MB 0.0488 → 50KB 0.1953 → 200KB 12.5 → 12.5MB 0.6835 → 700KB 0.0009765 → 1KB This parameter can be defined Content-Repository specific. 0.0 Convert Single to Multipage Tiff Checkbox If enabled, during runtime, single page-tiffs (data1, data2, etc. components) are converted to multipage tiff format for display. The document in the archive will not be changed. This parameter can be defined Content-Repository specific. Inactive Auto Decompress Checkbox When activated, the components are automatically decompressed. Inactive Allows you to define another decoding which will be used as a fallback in case the requested component's name wasn't encoded in UTF-8. e.g.: ISO-8859-1 ( You may find the available encodings here: https://docs.oracle.com/javase/8/docs/technotes/guides/intl/encoding.doc.html ) Usually (in DVS and KRPO) SAP encode the CompId twice. Therefore, we have to decode this CompId twice as well. But there are exceptions: For example the SAP module ECTR. This encode the compId only once. Same goes for the RSCMST (but this has no testcases for compId with special chars). To ensure most of the customers have the expected results (as most of them use KPRO and DVS), the Default is "active" Check Backend Mode Dropdown list If activated, when processing the serverInfo request, access to a random DocId for each Content-Repository is checked. This parameter can be defined Content-Repository specific. CAUTION: Only use this for troubleshooting! Off DMS Connection Keep Alive Checkbox Controls whether a DMS connection (object instance) should be closed (LinkClose) when a DMS exception occurs. Active: DMS connection is terminated (LinkClose) and then reopened (LinkOpen). Useful if DMS does not support the reconnect. Inactive: Do not end the DMS connection Active Timeout Requiring DMS Object (ms) Int If an instance of a DMS object no longer responds and new instances can no longer created because the limit has been reached from the Max Process Count parameter, then the time set here is waited (in seconds) until the suspended instance terminates and a waiting request is processed. 0: Timeout is deactivated 0 The active HTTP(S) Servlet Mapping endpoint for ArchiveLink. In case you need to address the Contentserver under another endpoint (like /ContentServer) you are able to configure the name here accordingly. Default: contentserver CAUTION: You have to restart the Application (or Webserver) before the changes take effekt. Exclude components from signing String Excludes individual components from signing. This parameter can be defined Content-Repository specific. Depends on the Sign and Verify Content settings in the Components section. note;kgsannotation;descr;pagelist Remote Function String Name of the SAP function module for processing the KeyExport function. Z_KGSKEYEXPORT BarcodeTimer Int (seconds) Parameter for activating the barcode upload from the DMS to SAP. The processing directory is located within the working directory: <WorkingDirectory>/Barcode/ For the communication via RFC, the necessary parameters must be maintained. IMPORTANT: Furthermore, this timer also activates and controls the processing interval for the KeyExport function! 0 ILM Repository String Name of a ILM „repository“ for the logical communication of data per the KGS CS interface. ILM User String User from the SAP ILM configuration (RFC destination) for the communication with the KGS CS. Password String Password from the SAP ILM configuration (RFC destination) for the communication with the KGS CS. Ignore past Retention Date Checkbox When activated, ILM PropPath requests that want to put the expiration_date attribute in the past are accepted. This feature may be useful when migrating ILM data. Inactive Enable ArchiveLink Reference check Checkbox This parameter can be activated if an ILM resource represents a reference to an ArchiveLink document and is to be blocked by expiration_date and legal_hold (PROPPATCH). Inactive Allow ILM Duplicates Checkbox When enabled, ILM Put requests that want to create a resource that already exists, will be answered successfully if the sizes coincide. Inactive: These ILM PUT requests are rejected Inactive Force Deletion Checkbox Attempts to deregister the corresponding ILM resource in the event of a faulty deletion. InactiveLicense
Barcode
Protocol
Common
During the initialization of the KGS CS, the table contents are read by the RFC using the login data.
The determination of document type is also applied to the Barcode function of the KGS CS.Security
Trusted X-Forward-For Servers String * rucd <servlet>/conf/contentserver/security RFC
Components
Fallback Encoding String Empty URLDecode twice Checkbox Active Set Content-Disposition for GET Checkbox Get responses will set an additional content-disposition header. Browser will use the value in the header as filename usually data.xxx. (since 5.3.8) False Backend
Servlet Mapping PathString String contentserver Content
Index Export
ILM
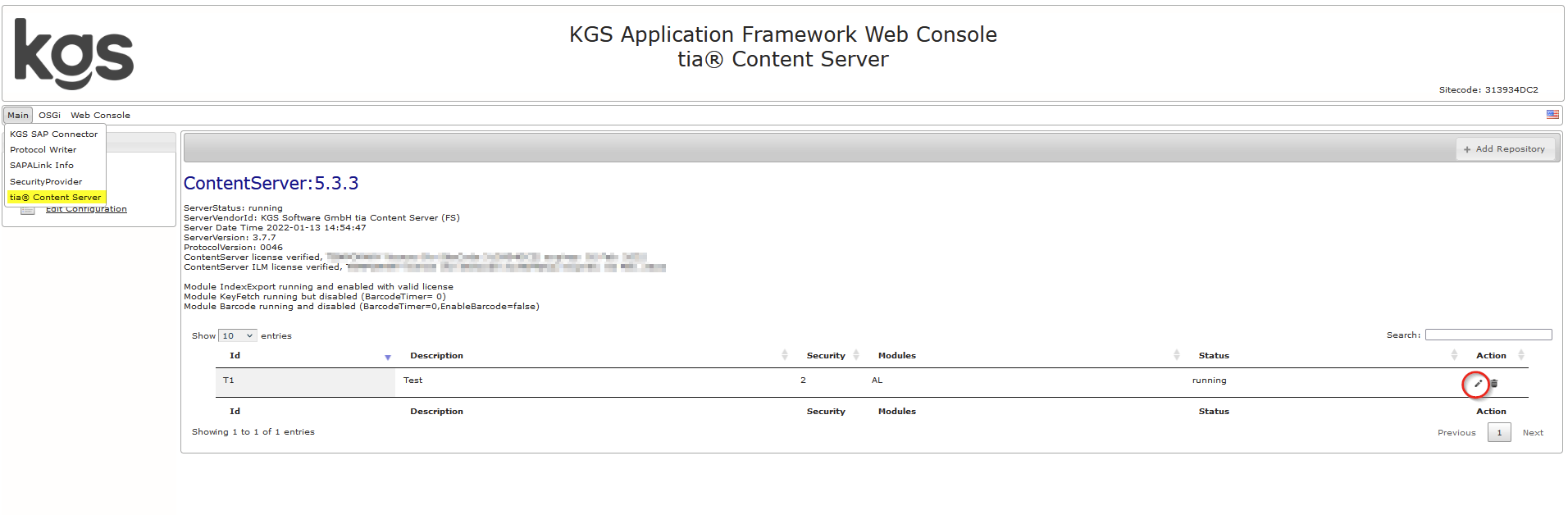
Configuration options for the repositories
Some parameters can be defined content repository specific. These can be set by following the menu option Main → ContentServer4ArchiveLink as shown below: Security Int 0: Security Inactive 1: Security Active 2: Security Active. Seperate administration via CSAdmin necessary This parameter can be defined Content Repository specific. CSV list of ArchiveLink requests (non-case sensitive), e.g. create, delete, update, etc. When a request that is maintained in this list arrives, the value set in the Security parameter is inverted to process this request. Example 1: Security=2 the SecKey procedure is active. SecurityChangeOnCommand=get,delete,info The incoming GET request is processed WITHOUT checking the SecKeys incl. Expiration. Example 2: Security=0 the SecKey procedure is not active. SecurityChangeOnCommand=get,delete,info The incoming GET request is processed WITH examination of the SecKeys incl. Expiration. This parameter can be defined Content Repository specific. Only the clients specified here (IPs or hostnames) may write to the archive (create, update etc.). If no client is specified, all clients may write. The parameter is to be created as a CSV list. If a client is not listed, they receive the RC 401 à unauthorized. This parameter can be defined Content Repository specific. Only the IP addresses or hostnames specified here (SAP server) are authorized to use the CSAdmin function in SAP. Requests from other IPs or hosts receive the RC 401 → unauthorized. This parameter is to be created as a CSV list. The last IP segment can be used a wildcard. For example; ContentServer.AllowedCSAdmin=sapadm,192.168.1.2,192.168.2.* This parameter can be defined Content Repository specific. RFC connection Dropdown Select the RFC connection configured in the KGS SAP Connector For older versions Enable Viewer Checkbox To use the tia® H5 Viewer (EN) with the KGS ContentServer, the Enable Viewer checkbox must be set within the desired repository. Viewer Context Dropdown list Name of the used KGS Viewer profile. Index Export Dropdown list Off: Function deactivated. Internal: Additional attributes of the documents are determined via the ContentServer after creation of a document by RFC (pull procedure). External: Additional attributes are transferred to the ContentServer (push procedure) via the SAP Event Mechanism. off Dropdown list If activated, when processing the serverInfo request, access to a random DocId for each Content Repository is checked. This parameter can be defined Content Repository specific. CAUTION: Only use this for troubleshooting! This Parameter can only be used from a Non-SAP Client! If a valid link is entered, a ArchiveLink GET-Request is redirected to the new target. The response will be handled directly by the target. The following fields are mandatory and substituted with the actual request Parameter: So, an Example would be: http://<Serveraddress>:<Port>/KGSAdmin-CS/contentserver?get&pVersion=0047&contRep={CONTENT_REP_ID}&docId={ARCHIVE_DOC_ID}&compId={COMPONENT_ID} which Results in a redirect for GET-Requests to the new Server. Caution: Only GET-Requests are forwarded. PUT and POST Requests will still be performed (and therefore archived) in the actual Contentserver. Also Non-KGS Servers can be used as Target. This Parameter can only be used from a Non-SAP Client! If a valid link is entered, a ArchiveLink GET-Request is forwarded to the new target. The response will be handled by the actual Content Server. The following fields are mandatory and substituted with the actual request Parameter: So, an Example would be: http://<Serveraddress>:<Port>/KGSAdmin-CS/contentserver?get&pVersion=0047&contRep={CONTENT_REP_ID}&docId={ARCHIVE_DOC_ID}&compId={COMPONENT_ID} which Results in a redirect for GET-Requests to the new Server. Caution: Only GET-Requests are forwarded. PUT and POST Requests will still be performed (and therefore archived) in the actual Content Server. Also Non-KGS Servers can be used as Target. Sign and Verify Content Checkbox Creates a hash value and signs this with a timestamp. When the data is called, the hash value is verified against the signature. This parameter can be defined Content Repository specific. Inactive SecurityProvider Dropdown list Currently only timestamp signatures with certificate are available. This parameter can be defined Content Repository specific. TrustedTimestamp with Certificate Excludes individual components from signing. Compression Size (Mb) Double Defines that components equal or greater than the value specified here (in MB) should be compressed. This function is only supported if the DMS supports the “DMS_COMP_PROPERTY_COMPRESSI ONSTRING” property. For example: 1 → 1 MB 0.0488 → 50KB 0.1953 → 200KB 12.5 → 12.5MB 0.6835 → 700KB 0.0009765 → 1KB This parameter can be defined Content Repository specific. 0.0 CSV list of MimeTypes that should be compressed. If this parameter is not defined, the compression will be applied to all MimeTypes (=*). For example; CompressMimeType=application/pdf,image/tiff Apart from MimeTypes, document types can also be defined, if the SAPMimeExtentionLookup parameter was configured. The MimeType for the document category is then determined by RFC using the SAP table TOADD. This parameter can be defined Content Repository specific. Convert Single to Multipage Tiff Checkbox If enabled, during runtime, single page-tiffs (data1, data2, etc. components) are converted to multipage tiff format for display. The document in the archive will not be changed. This parameter can be defined Content Repository specific. InactiveSecurity
SecurityChangeOnCommand Allowed Clients Allowed CSAdmin Clients RFC
Viewer
Index Export
Common
Description Description for the specific Content Repository Disable Delete Delete requests will not be processed/rejected for this Content Repository. Backend
Check Backend Mode Off HTTP
Parameter Name DataType Description Default GET HTTP Redirect String Empty GET HTTP Forward String Empty Components
Exclude Components from signing String note;kgsannotation;descr;pagelist Compression Mime Types String
Configuration for SAP communication
For features like getting MimeTypes & IndexDownload, you need to configure the RFC connection for the SAP server. Please keep in mind that you have to provide the SAP JCo, before you can use these features: Install SAP Java Connector (SAP JCo) Create a SAP Connection & select it in the RFC tab inside the ContentServer main-configuration or Content Repository specific configuration.SAP Connector configuration (newer than v5.1.0)
RFC configuration (until v5.1.0)
SAP-Customizing and ArchiveLink Security
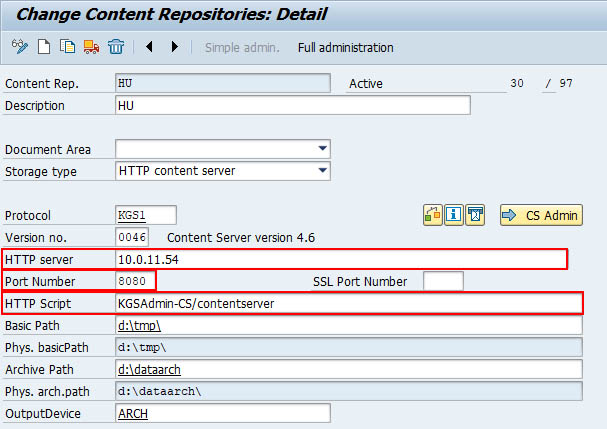
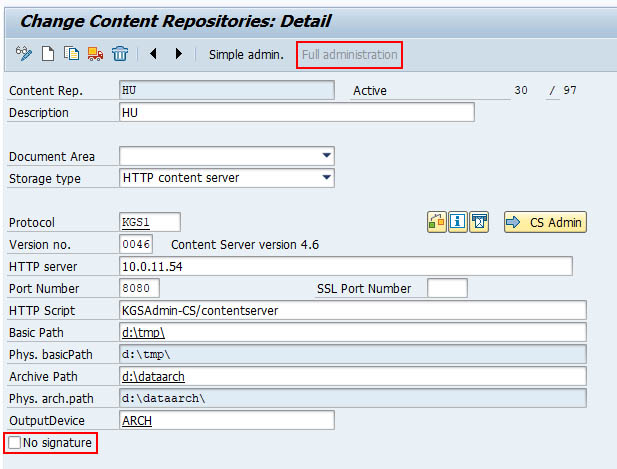
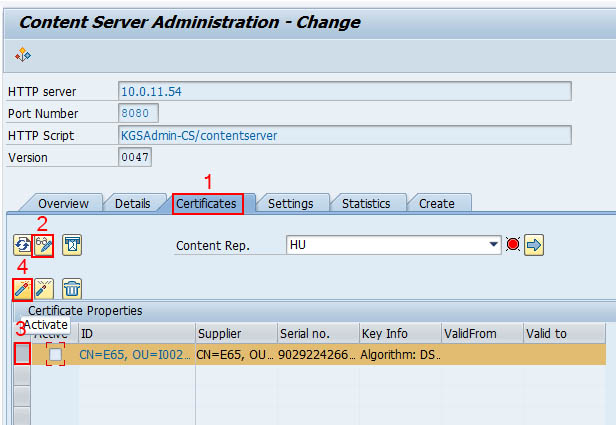
KGS CS is configured within SAP using the definition of Content Repositories. The transaction is OAC0. Following parameters have to be set: To use the ArchiveLink security you have to enable the signature and send (& activate) the certificate to the Content Server. To see the signature parameter, you have to access the Full administration. To use the security No signature needs to be unchecked. To send the certificate click on the envelope button. This sends a putCert request to the Content Server. In case you use the security in mode 2, you have to activate the certificate by hand.OAC0 - Content Repository configuration
ArchiveLink Security (OAC0)
Activating a certificate
Logging for tia® Content Server
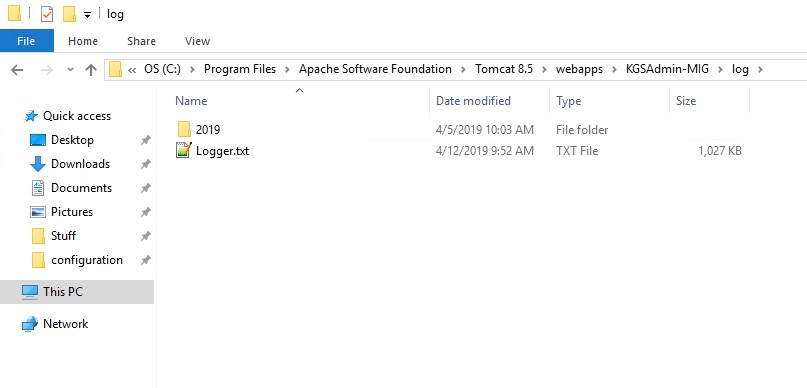
The defaultname for the logfile is "Logger.txt" and contains the log information from all applications inside the servlet installation. Without a change the file is located inside the "log" folder of the servlet. Example for Tomcat Webserver on Windows:
Troubleshooting
- Corrupt PDF files after archiving via SAP
- Time of the contentserver is wrong
- tia® Content Server cannot access existing archived documents